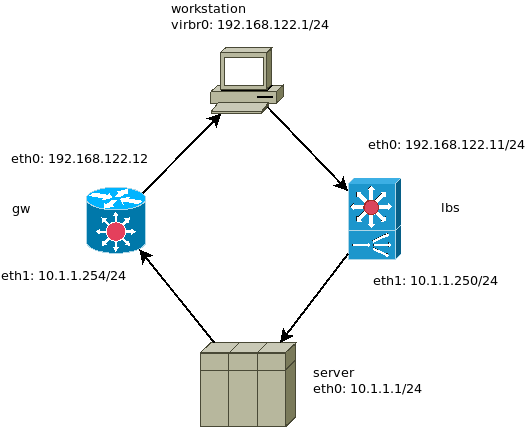

DIY DNAT – catch all TCP packets, not only SYN
flush ruleset
table ip diy-dnat {
chain prerouting {
type filter hook prerouting priority mangle;
iif eth0 tcp dport 80 notrack ip daddr set 10.1.1.1;
iif eth0 tcp dport 1234 notrack ip daddr set 10.1.1.1;
iif eth0 udp dport 1234 notrack ip daddr set 10.1.1.1;
iif eth0 tcp dport 2201 notrack ip daddr set 10.1.1.1 tcp dport set 22;
}
}
DIY SNAT – catch all TCP packets, not only SYN – and spoof lbs' IP address (needed for both TCP and UDP)
flush ruleset
table ip diy-snat-spoof {
chain postrouting {
type filter hook postrouting priority mangle;
oif eth0 ip saddr 10.1.1.1/32 tcp sport 22 tcp sport set 2201
oif eth0 ip saddr 10.1.1.0/24 notrack ip saddr set 192.168.122.12
}
}
we are just checking that SNAT+SPOOF works for now.
send some requests from workstation
curl -I 192.168.122.12 ssh 192.168.122.12 -l root -p 2201
sniff what is coming out as an answer on gw
tcpdump -ni eth0 not tcp port 22 04:33:25.450833 IP 192.168.122.12.80 > 192.168.122.1.44252: Flags [S.], seq 47328729, ack 2311807596, win 65160, options [mss 1460,sackOK,TS val 2345412055 ecr 3985664520,nop,wscale 5], length 0
==> so far so good, we now see 192.168.122.12 instead of 10.1.1.1, eventhough we’re on established TCP
on server
ncat -ulvp 1234 -e /bin/bash
on workstation
ncat -nvu 192.168.122.12 1234 echo test ok
==> works, we are spoofing 192.168.122.12 alright
on server
ncat -lvp 1234 -e /bin/bash
on workstation
ncat -nv 192.168.122.12 1234 echo test ok
==> works after enabling diy-dnat (diy-snat-spoof was not enough as we were getting RSTs)