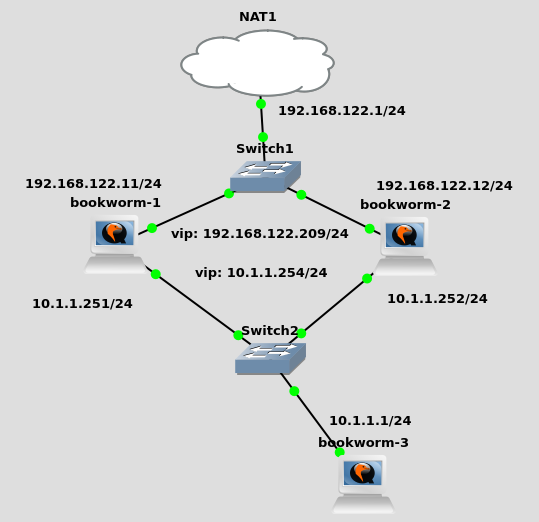
install | setup | routing states
tested on debian12

this sample goes along with a keepalived setup
flush ruleset
table inet filter {
chain forward {
type filter hook forward priority filter; policy drop;
ip protocol icmp accept
ct state invalid log prefix "FORWARD INVALID: " drop
ct state new,established,related accept
log prefix "FORWARD DROP POLICY: "
}
}
table ip nat {
# DNAT
chain prerouting {
type nat hook prerouting priority dstnat;
iif eth0 tcp dport 2222 dnat 10.1.1.1:22
}
# SNAT
chain postrouting {
type nat hook postrouting priority srcnat;
ip saddr 10.1.1.0/24 oif eth0 snat 192.168.122.209
}
}
General {
HashSize 8192
HashLimit 65535
LockFile /var/lock/conntrackd.lock
UNIX {
Path /var/run/conntrackd.sock
Backlog 20
}
SocketBufferSize 262142
SocketBufferSizeMaxGrown 655355
Systemd on
Syslog off
LogFile on
Filter {
Protocol Accept {
TCP
}
Address Ignore {
IPv4_address 127.0.0.1
IPv6_address ::1
# ignore front-facing local address
IPv4_address 192.168.122.11/32
#IPv4_address 192.168.122.12/32
# ignore internal local address
IPv4_address 10.1.1.251/32
#IPv4_address 10.1.1.252/32
}
}
}
Sync {
Mode NOTRACK {
# active / active
DisableExternalCache on
StartupResync on
}
UDP {
IPv4_address 10.1.1.251
#IPv4_address 10.1.1.252
IPv4_Destination_Address 10.1.1.252
#IPv4_Destination_Address 10.1.1.251
Port 3780
Interface eth1
Checksum on
}
}
testing DNAT and SNAT states at once