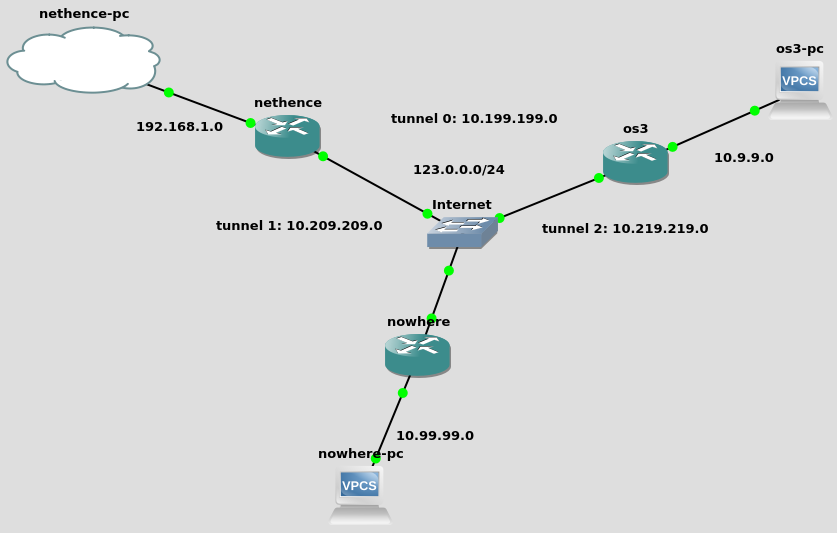
assuming gns3 c7200 dynamips appliances

internal and mgmt interface
setup
basic mgmt setup
(passwords...)
snmp? yes
mgnt interface --> fa0/1
fdx yes
! nethence
192.168.1.254/24
! os3
10.9.9.254/24
! nowhere
10.99.99.254/24
front-facing/public interface
conf terminal
interface fa0/0
! nethence
ip address 123.0.0.1 255.255.255.0
! os3
ip address 123.0.0.2 255.255.255.0
! nowhere
ip address 123.0.0.3 255.255.255.0
no shutdown
exit
check
! os3-pc set pcname os3-pc ip 10.9.9.1/24 10.9.9.254 save ping 10.9.9.254 ! nowhere-pc set pcname nowhere-pc ip 10.99.99.1/24 10.99.99.254 save ping 10.99.99.254 ! nethence-pc ping 192.168.1.254 route add -net 10.9.9.0/24 gw 192.168.1.254 route add -net 10.99.99.0/24 gw 192.168.1.254 ! nethence ping 123.0.0.2 ping 123.0.0.3 ! os3 ping 123.0.0.3 write memory
between nethence and os3
crypto isakmp policy 1
encryption aes
authentication pre-share
group 2
point to the neighbor
! nethence
crypto isakmp key beep-beep address 123.0.0.2
! os3
crypto isakmp key beep-beep address 123.0.0.1
crypto ipsec transform-set some-transport-set esp-aes esp-sha-hmac
mode tunnel
crypto ipsec profile some-ipsec-profile
set transform-set some-transport-set
define the tunnel interface
interface tunnel 0
! nethence
ip address 10.199.199.1 255.255.255.0
tunnel source 123.0.0.1
tunnel destination 123.0.0.2
! os3
ip address 10.199.199.2 255.255.255.0
tunnel source 123.0.0.2
tunnel destination 123.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile some-ipsec-profile
you should see this appearing in the console
%LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up
static routes and enable routing
! nethence ip route 10.9.9.0 255.255.255.0 tunnel 0 ip routing ! os3 ip route 192.168.1.0 255.255.255.0 tunnel 0 ip routing
check and save router configuration
! nethence-pc ping 10.9.9.1 write memory
between nethence and nowhere
nethence
conf terminal
crypto isakmp key beep-beep1 address 123.0.0.3
interface tunnel 1
ip address 10.209.209.1 255.255.255.0
tunnel source 123.0.0.1
tunnel destination 123.0.0.3
tunnel mode ipsec ipv4
tunnel protection ipsec profile some-ipsec-profile
end
nowhere
conf terminal
crypto isakmp policy 1
encryption aes
authentication pre-share
group 2
exit
crypto isakmp key beep-beep1 address 123.0.0.1
crypto ipsec transform-set some-transport-set esp-aes esp-sha-hmac
mode tunnel
exit
crypto ipsec profile some-ipsec-profile
set transform-set some-transport-set
exit
interface tunnel 1
ip address 10.209.209.3 255.255.255.0
tunnel source 123.0.0.3
tunnel destination 123.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile some-ipsec-profile
end
static routes and enable routing
! nethence ip route 10.99.99.0 255.255.255.0 tunnel 1 ! nowhere ip route 192.168.1.0 255.255.255.0 tunnel 1 ip routing
check and save router configuration
! nethence-pc ping 10.99.99.1 write memory
between os3 and nowhere
os3
conf terminal
crypto isakmp key beep-beep2 address 123.0.0.3
interface tunnel 2
ip address 10.219.219.2 255.255.255.0
tunnel source 123.0.0.2
tunnel destination 123.0.0.3
tunnel mode ipsec ipv4
tunnel protection ipsec profile some-ipsec-profile
end
nowhere
conf terminal
crypto isakmp key beep-beep2 address 123.0.0.2
interface tunnel 2
ip address 10.219.219.3 255.255.255.0
tunnel source 123.0.0.3
tunnel destination 123.0.0.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile some-ipsec-profile
end
more static routes
! os3 ip route 10.99.99.0 255.255.255.0 tunnel 2 ! nowhere ip route 10.9.9.0 255.255.255.0 tunnel 2
check and save router configuration
! os3-pc ping 10.99.99.1 write memory
%CRYPTO-6-IKMP_MODE_FAILURE: Processing of Informational mode failed with peer at 123.0.0.1 Tunnel0 is up, line protocol is down
==> double check neighbor address and that sets/tags do match
Cisco IPsec VPN Hardware for Cisco 7200 Series Routers At-A-Glance https://www.cisco.com/c/dam/en/us/products/collateral/interfaces-modules/vpn-acceleration-module-2-plus/at_a_glance_c45-466108_v1.pdf
Chapter: Site-to-Site and Extranet VPN Business Scenarios https://www.cisco.com/c/en/us/td/docs/security/vpn_modules/6342/vpn_cg/6342site3.html
Cisco IPsec Easy VPN Configuration https://networklessons.com/uncategorized/cisco-ipsec-easy-vpn-configuration/
How To Use VPCS in GNS3 https://protechgurus.com/how-to-use-vpcs-in-gns3/
IPSec Static Virtual Tunnel Interface https://forum.networklessons.com/t/ipsec-static-virtual-tunnel-interface/2374/7
IPSec Static Virtual Tunnel Interface https://networklessons.com/cisco/ccie-routing-switching-written/ipsec-static-virtual-tunnel-interface/
Quick Configs - Dynamic VTI IPsec (virtual-template, unnumbered, keyring, isakmp) https://www.youtube.com/watch?v=c1FyP71dVOE
#100DaysOfLabbing - Day 1 & 2 https://showipintbri.blogspot.com/2018/07/100daysoflabbing-day-1-2.html
%CRYPTO-6-IKMP_MODE_FAILURE: Processing of Informational mode failed with p https://community.cisco.com/t5/other-security-subjects/crypto-6-ikmp-mode-failure-processing-of-informational-mode/td-p/90618
Cisco System Messages https://www.cisco.com/c/en/us/td/docs/ios/system/messages/guide/consol_smg.html
Chapter: Cisco System Messages Overview https://www.cisco.com/c/en/us/td/docs/ios/system/messages/guide/consol_smg/sm_cnovr.html