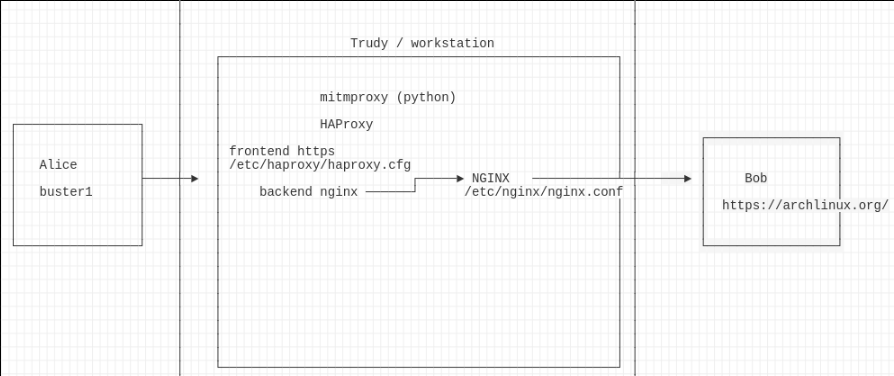

setup HAProxy as usual plus some additional tuning
vi /etc/haproxy/haproxy.cfg
frontend http
bind *:8080 alpn h2,http/1.1
http-response set-header Strict-Transport-Security "max-age=16000000;"
redirect scheme https code 301
frontend https
bind *:8443 ssl crt /root/certs/buster2.crt alpn h2,http/1.1
http-response set-header Strict-Transport-Security "max-age=16000000;"
default_backend servers
backend servers
server archlinux archlinux.org:443 ssl verify none
check and apply
haproxy -c -f /etc/haproxy/haproxy.cfg systemctl restart haproxy.service netstat -lntup | grep :8
then enable the interception, here assuming a KVM otherwise GNS3 host
nic=virbr0 iptables -t nat -A PREROUTING -i $nic -p tcp --dport 80 -j REDIRECT --to-port 8080 iptables -t nat -A PREROUTING -i $nic -p tcp --dport 443 -j REDIRECT --to-port 8443 iptables -nvL -t nat
from the victim
echo Q | openssl s_client -connect archlinux.org:443 | openssl x509 -noout -text curl -i https://archlinux.org/ curl -ik https://archlinux.org/
so we’re seeing encrypted sessions. Now is the time to think about ways to get clear-text.
TODO ssl session file
tested: WORKS
vi haproxy.cfg
backend servers
server localhost localhost:80
install nginx and point to target
vi default.conf
server {
listen 80;
server_name archlinux.org;
location / {
proxy_pass https://archlinux.org/;
}
}
TODO memory vs. strace
HAProxy TLS interception https://discourse.haproxy.org/t/haproxy-tls-interception/6365
http://www.squid-cache.org/Doc/config/proxy_protocol_access/
https://wiki.squid-cache.org/Features/HTTPS#Encrypted_browser-Squid_connection ==> see Encrypted browser-Squid
How to link frontend to backend when the path request are different? https://stackoverflow.com/questions/54408137/how-to-link-frontend-to-backend-when-the-path-request-are-different