
For hosting e.g. @nethence.com, setup an HTTPS vhost as such
vi /etc/nginx/conf.d/sts.conf
server {
listen 80;
listen [::]:80;
server_name mta-sts.nethence.com;
location / {
return 301 https://nethence.com/smtp/;
}
# deal with http-01 challenges (no http2 there)
location ^~ /.well-known/acme-challenge/ {
default_type "text/plain";
# trailing slash matters
alias /var/www/dehydrated/;
}
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name mta-sts.nethence.com;
ssl_certificate /etc/dehydrated/certs/mta-sts.nethence.com/fullchain.pem;
ssl_certificate_key /etc/dehydrated/certs/mta-sts.nethence.com/privkey.pem;
ssl_certificate /etc/dehydrated/certs/ECC/mta-sts.nethence.com/fullchain.pem;
ssl_certificate_key /etc/dehydrated/certs/ECC/mta-sts.nethence.com/privkey.pem;
location / {
return 301 https://nethence.com/smtp/;
}
location /.well-known/ {
root /data/www/$server_name;
index index index.html index.htm;
try_files $uri $uri/ =404;
}
autoindex off;
location = /robots.txt { access_log off; log_not_found off; }
location = /favicon.ico { access_log off; log_not_found off; }
location ~ /apple-touch-icon { access_log off; log_not_found off; }
}
then define the STS policy e.g.
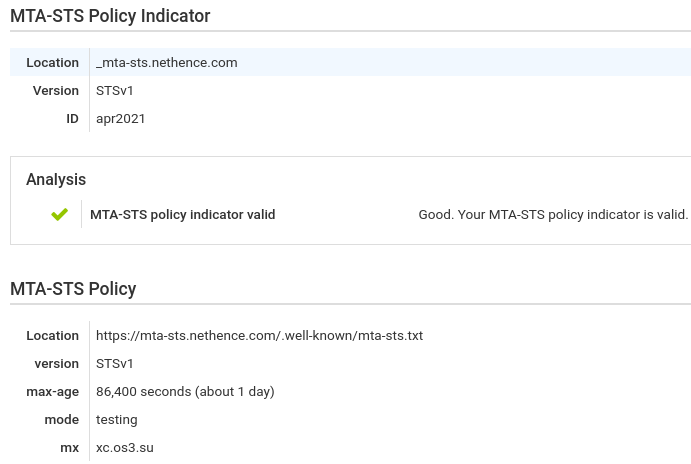
vi /data/www/mta-sts.nethence.com/.well-known/mta-sts.txt version: STSv1 mode: testing mx: xc.nethence.com max_age: 86400
define DNS entries for that purpose
; STS _mta-sts IN TXT "v=STSv1; id=apr2021" _smtp._tls IN TXT "v=TLSRPTv1; rua=mailto:abuse@nethence.com"
and validate remotely
host -t txt _mta-sts.nethence.com host -t txt _smtp._tls.nethence.com curl -i https://mta-sts.nethence.com/.well-known/mta-sts.txt
is that really necessary?…
SMTP HEALTH CAMPAIGN https://nethence.com/smtp/
Introducing MTA Strict Transport Security (MTA-STS) https://www.hardenize.com/blog/mta-sts
MTA-STS https://www.rfc-editor.org/rfc/rfc8461.txt
Gmail making email more secure with MTA-STS standard https://security.googleblog.com/2019/04/gmail-making-email-more-secure-with-mta.html
[exim] MTA-STS Solution https://lists.exim.org/lurker/message/20190508.162714.e1b28207.en.html
[exim] MTA-STS and Server Name Indication (SNI) on mail servers https://www.mail-archive.com/exim-users@exim.org/msg54684.html